General recommendations
Since safety of our clients data is our top priority, every day we strive to ensure their safety and confidentiality by applying the latest technology and top security standards. Considering that, unfortunately, everyday all around the globe and in our country we witness new ways of committing fraud, this document will give recommendations on how to protect your data.
The recommendations provided below will not only help you use digital channels of Banca Intesa in safe manner, but will also help you with everyday use of other online services, such as e-mail, social media and other content.
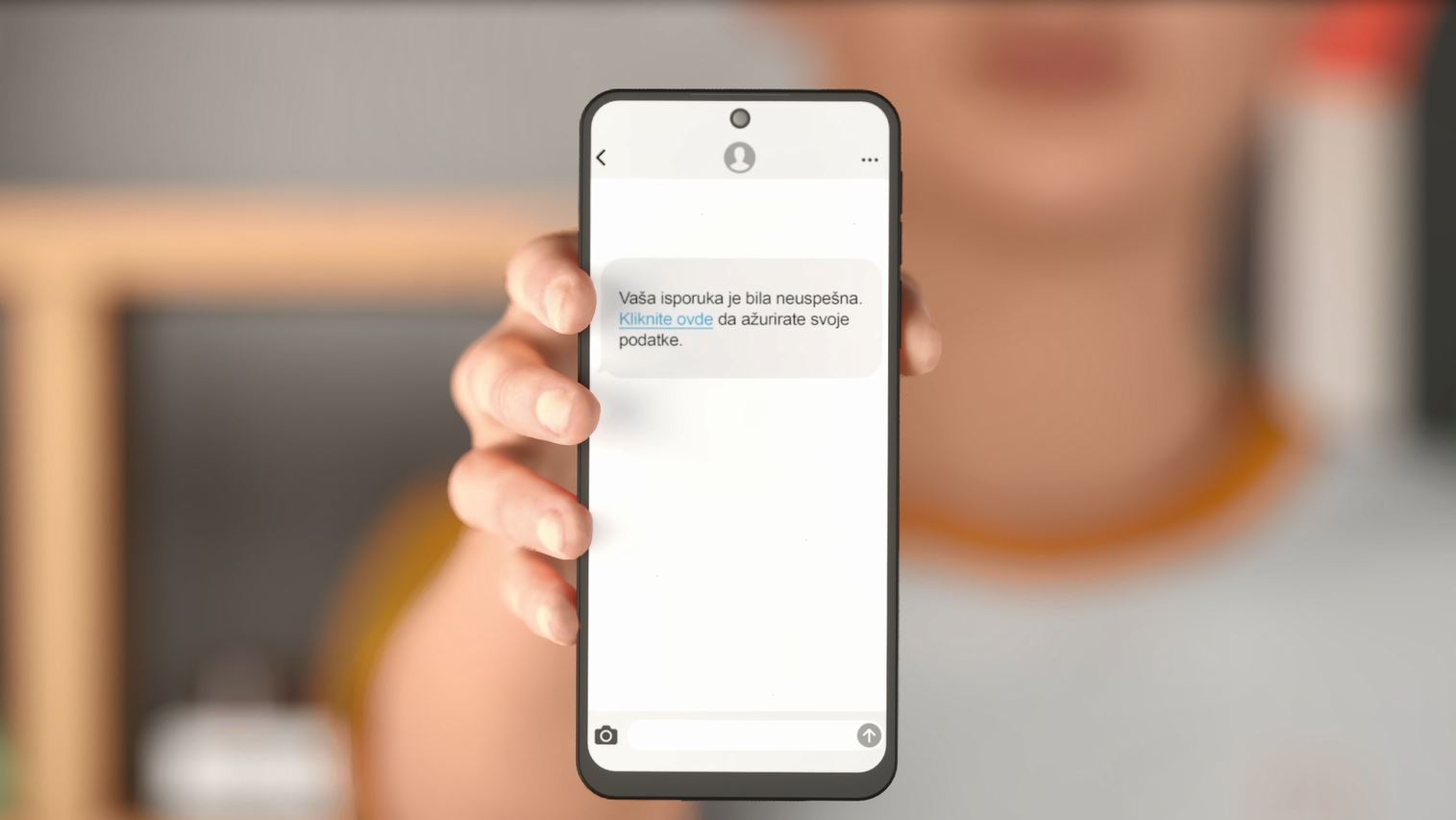
WHATS UP/VIBER/SMS scams
There is a current fraud scheme on WHAT'S UP VIBER, SMS.
The messages request an urgent payment of funds to help a friend.
In reality, it is a scam where the attacker submits a picture of a payment card with an account number that does not belong to the person from whose number the message was sent.
- The main indicator of fraud.
Urgent payment request to help a friend
- How to protect yourself:
- Before making a payment, be sure to contact the person requesting the payment
- Do not pay money according to instructions received via Whats up, Viber, SMS because they contain the accounts of attackers, not friends.
- Be careful with the messages you receive via Whats up, Viber, SMS
- If you have already paid the funds - report the case to the competent authorities and inform the bank
Investment scams
The fraud scheme, called OKE GREEN, is aggressively promoted through social media, TikTok, Instagram and Telegram groups.
It is advertised as a modern investment platform for the development and improvement of AI systems.
In reality, it is a classic pyramid scheme. There is no platform, no AI mechanism, and no payout system. Everything takes place through messages in closed groups and falsely portraying the "success" of other members.
How does OKE GREEN work?
1. After you click on an ad on social networks, register and leave your contact information, "agents" appear to give you further notifications and instructions for "investing". Communication takes place exclusively through closed chat groups in various applications, led by people posing as AI experts.
2. Depending on the payment amount, the "company" assigns levels ("AI 1", "AI 2", "AI 3"... to "AI 5"). The higher the level, the higher the promised daily earnings.
3. To unlock higher levels, the user must:
- invest additional funds or
- bring in new members
4. When the user tries to withdraw money, excuses start and additional demands are made in the form of new and increasing payments and bringing in new members. If the user refuses to fulfill the new requirements, he is removed from the group and all contact ends, but without refund of the invested money.
The main indicators of fraud:
- Fast, easy and guaranteed additional income with AI technology is promised, without explaining how to make a profit.
- Payments and alleged payments go directly to and from various natural persons
- There are investment levels (AI 1–5) that require increased payments and bringing in new users.
- Fake payout screenshots and "financial freedom" ads are used.
- The platform is not registered with any financial regulator in Serbia or the EU.
How to protect yourself:
- Do not pay money on the instructions of unknown persons, to the accounts of unknown natural persons.
- Be careful with platforms that use terms like AI, green project, smart investment - this is often just a marketing mask.
- If someone invites you to "build a team" or "invite friends", it is a pyramid scheme.
- Check whether the company is registered with the National Bank of Serbia or another relevant regulator.
- If you have already paid the funds - report the case to the competent authorities and notify the bank at the nearest branch or the Bank's Contact Center at phone number 011/310 88 88.
General safety recommendations
- It is not recommended to use public or unsecured computers to login to digital banking applications (e.g. computers in hotels or internet cafes).
- Every time you log in check date and time of the previous login.
- Check your account balance and transaction details regularly (daily checks are recommended) to verify payment details, as well as other information about transactions; if you discover any suspicious transaction, please report it to the Bank immediately. If you don’t use digital channels of Banca Intesa to perform transactions activate them for overview of your accounts so you could timely identify suspicious transactions.
- Register your mobile phone number at the Bank teller and enable SMS notifications about bank balance changes and payment card transactions.
- Do not use your personal number, account number or any other personal or account information to create short name for your account in digital channels applications.
- Never leave your computer unattended while using Bank’s digital channels.
- We recommend that you never perform banking transactions while having several different internet browsers open on your computer.
- Always properly log out from Bank’s digital channel application by using the appropriate logout command. Closing internet browsers doesn’t always mean that you’ve been logged out from the system (session is interrupted).
How to avoid phishing, spyware and malware
All e-mails from Banca Intesa will always be sent from mail@bancaintesa.rs and info@mail.bancaintesa.rs.
All messages containing sensitive data forwarded by Banca Intesa will be protected by digital signature.
Banca Intesa will never ask you to provide confidential data by e-mail, SMS or phone and will never send you a link requesting you to enter confidential data, such as: User ID, PIN, payment card details and other confidential data. If you receive such e-mail, SMS or telephone call, please contact the Bank immediately through official Contact Centre (011 310 88 88).
ATTENTION:
Protect yourself from those who present themselves as Banca Intesa employees (online or over the phone) and ask you for information that can then be used by them in an unauthorized manner.
A third party can contact you by phone and request information from you such as username, password, PIN, payment card data (number combined with validity date), which can then be used in an unauthorized manner.
They can also contact you via email or SMS and ask for your confidential information. These messages are, graphically and substantively, very similar to those you use in communication with the bank or another institution, and aim to steal confidential and sensitive information from you and commit fraudulent financial transactions and fraud.
Examples of attempted fraud
BANCA INTESA COMMUNICATES VIA
- e-mail: mail@bancaintesa.rs and info@mail.bancaintesa.rs
- SMS: BancaIntesa
- Social media: Facebook, Instagram, Twitter, YouTube i LinkedIn
- Phone: + 381 66 894 60 00 ili + 381 66 894 69 99
TIPS
- Bookmark the links to Banca Intesa, Banca Intesa e-banking and Banca Intesa Secure in your internet browser and access these websites via bookmarks only, never by clicking on a link from suspicious email.
- Do not open e-mails from unknown senders. Always be suspicious about e-mails that are allegedly sent by a financial institution, state institution or any other agency that requests your login details, your account or payment card details or requests you to verify your account or credentials for access to Bank’s digital channels, such as username, password, PIN code and similar data. If you open files attached to an email or click on a link from suspicious e-mail your computer may get infected by malware, which will allow hackers to take full control of your computer and have full access to all confidential data stored in the computer.
- Never respond to suspicious e-mails and never click on links in the e-mail body. Contact the alleged sender if you doubt his legitimacy.
- Install anti-virus software and firewall, as well as spyware and malware detection software and update them regularly.
- Regularly install patches for your computer’s operating system, update operating system and key applications.
- Check your internet browser settings and select at least medium level of security.
- When you access websites (including Bank’s e-banking site) that are protected by transport encryption (e.g. csl/tls protocol, https in the link) make sure to check the associated digital certificate for time validity (i.e. if it has expired), check if the certificate has been issued by trusted certification body that is recognized as trusted by your internet browser, as well as if the certificate is issued for the link your accessing (i.e. is the link contained in the subject field of the certificate). Follow the link only after successfully checking all the above.
- Regularly backup the data that is the most critical for the tasks you perform on computer, because that is the only safe way of staying protected from possible ransomware attacks. If nevertheless you become a victim of such attack, never accept the blackmail and never pay the ransom to the criminals.
How to avoid emails getting intercepted
- The malicious users may intercept business correspondence between foreign supplier and domestic buyer (legal entity), change details in the foreign invoice, replace the account of the foreign supplier with a third-party account that may be accessed by malicious users.
- Do not use free e-mail services for business correspondence.
- Install and regularly update your operating system, anti-virus software and firewall on your computer.
- Send confidential and personal information, as well as any business correspondence, by protected e-mails only.
- If you use e-mail to exchange business-related documents that may contain confidential information with the Bank, please check with your contact person in the Bank (employee of the bank responsible for communication with your), if it is possible (and how) to fully protect the e-mail communication between you and the Bank in order to prevent leaking of confidential data (personal or corporate) through this communication channel.
- Do not use public computers (internet cafe) to perform business tasks.
- Before you pay foreign invoices of significant value, always confirm and verify payment instructions with the issuer (foreign supplier).
- After paying a foreign invoice, always check with the issuer if the transaction has been successfully completed.
Recommendations on configuration of home WiFi
Wireless network (WiFi) may create an “open door” for unauthorised access to your computer network.
If you use home WiFi network, it is recommended to secure in the following way:
- Change administrator password of WiFi device from factory default to strong password. Write down new password and keep it at safe location, because you may need it to configure your WiFi device in the future.
- Disable remote administration of WiFi device.
- If acceptable, disable broadcast of your wireless network SSID.
- Enable WPA (or WPA2) encryption and define WPA password for access to your WiFi network.
- If only known computers or mobile devices will access your WiFi network, consider enabling MAC filter on your device. Each computer or any other device with network card will have factory assigned unique MAC address. MAC filter will allow only devices with registered MAC address the network.
Recommendations for mobile banking
- Immediately report to the Bank any loss, theft, fraud, unauthorized use, change or cancellation of mobile phone number and mobile device (mobile phone or tablet) on which you use authentication means and m-banking services, either by visiting the Bank or via official Contact Centre of the Bank.
- Avoid using unsafe WiFi networks, such as open and public WiFi networks, to carry out banking transactions or to check accounts. Instead, if no safe WiFi network is available, always use mobile data network for m-banking services on your mobile device (mobile phone or tablet).
- Download and install apps only from official Apple, Google Play or Huawei stores.
- Install and regularly update your operating system, anti-virus software and firewall on your mobile device.
- Restrict access to your mobile phone by appropriate password or any other security parameter (fingerprint or face recognition).
- Never use password from your social media as an access password for your phone or phone apps.
- Turn off Bluetooth and NFC, when you’re not using them. They may be used for unauthorized access to confidential data stored on your mobile device.
- Activate encryption on mobile device to protect confidential data.
Investment scams
Misuse of funds and accounts on mobile and electronic banking applications through fraudulent investment offers
WHEN AN OFFER IS TOO GOOD TO BE TRUE...
Imagine that you invest 250 euros, and every month you have 1,000 euros of passive income in your account. Sound tempting? However, promises like this are the first warning sign. When someone guarantees fast and safe earnings - be careful. Sophisticated attacks with the aim of identity theft, your data and money, are often hidden behind such offers.
With the development of artificial intelligence, attackers increasingly use social networks and digital channels to spread the so-called investment frauds. These attacks often misuse the names of celebrities and companies to create a false sense of trust.
WHAT AN INVESTMENT FRAUD LOOKS LIKE - STEP BY STEP
1. A false ad that attracts attention
The attack most often starts through ads on social networks, search engines or in comments under popular posts. Ads are visually appealing and often include:
- photos of celebrities with false statements about "safe investments"
- logos of well-known banks, investment funds or technology companies
- headlines like: Invest €250 today and get €1,000 monthly passive income;The Secret Investment That Banks Don't Want You To Know; Automated trading system that guarantees profit.
The aim of the ad is to arouse curiosity and trust, so that the user clicks and starts the registration process.
2. Registration and first contact
By clicking on the ad, the user is redirected to a fake platform that imitates the appearance of a legitimate investment site. There, it is required to enter basic data (name, surname, email, phone number). Soon after, the victim is contacted by a person posing as a "broker", usually through messaging apps and calls.
Attackers use convincing stories about safe investments and quick earnings. Communications include multiple persons posing as "brokers," "bankers," or "legal advisors." The goal of this phase is to build trust and create a sense of urgency, so that the user invests money as soon as possible and continues to follow the attacker's instructions.
3. Payment of the initial deposit
The user (victim) is most often required to pay an initial deposit in the amount of 250 to 500 euros, as a "first step" towards activating the investment order. Payments are most often made:
- through payment cards, by entering data directly on a fake platform, or
- by transferring funds to the accounts of various natural persons, which the attackers use as intermediaries (the so-called "money mule").
This is the first moment when attackers get their hands on real money and test the victim's willingness to cooperate.
4. Fake Platforms Showing "Earnings" Growth
After payment, the victim is provided with access to a fake investment platform - a visually convincing application or website that simulates the growth of an investment. Showing:
- "account balance" that grows daily
- fictitious transactions and performance charts
- display of "gains" in thousands of euros
These platforms are completely under the control of attackers and have no connection with the real market. Their purpose is to create a false sense of success for users, in order to proceed with additional payments and allow attackers deeper access - including installing remote control applications and sharing access data.
5. Payment of funds - a false sense of success
In order to further convince the user (victim) that the investment is successful, attackers often redirect inflows from the accounts of other victims to the account of the person they are currently processing. These transactions are presented as "trading earnings" or "investment profits", further cementing a false sense of success.
6. Installation of remote access applications
Attackers demand the installation of apps that give them full control over the user's phone – including access to banking apps, passwords and security features.
7. The attacker's ultimate goal: complete financial exploitation
After gaining access to an electronic banking account, attackers use the user's account as a "money mule" - an intermediary to divert funds from other frauds. In the final stage, they aim for maximum financial exhaustion of the user, including:
- withdrawal of all available funds from the account
- realization of online loans and permitted payment account overdrafts on behalf of the user (victim)
- transferring money to other accounts, often linked to other victims
The user (victim) often becomes aware of the fraud only when he is already in a serious financial problem, with debts that he unwittingly made possible.
8. Secondary fraud - "refund"
After some time, the same attackers call again, posing as "international agents" who can help recover the money. They demand additional payments for "fees", and often blackmail the victim, accusing her of money laundering, forcing her to pay them even larger sums.
PROTECTION RECOMMENDATIONS
- Ignore suspicious ads and links
- Never share the security elements you receive from the bank - including SMS OTP codes, PINs, passwords, as well as authorization codes from the application
- Do not install remote access applications
- Change passwords immediately if you suspect a compromise
- Do not respond to "refund" offers
- Do not use your bank account for transactions on behalf of third parties
- Do not participate in transactions for which you do not know the exact purpose and origin of the funds
- Pay attention to unusual inflows and outflows
- Earnings do not come from unknown natural persons
- Do not allow your account to be used as a so-called money mule
- Buy and sell cryptocurrencies exclusively through registered and licensed brokers
NOTE ON RESPONSIBILITY AND PROCEDURE
Customers are fully responsible for all transactions they make through their accounts.
Before any transaction, it is necessary to be completely sure of its legality, purpose and identity of the other party.
Participating in transactions that later prove to be part of a fraudulent scheme does not absolve the client from liability.
If you have any doubt that you are part of such a scenario — immediately contact the nearest branch or the Bank's contact center at phone number 011/310 88 88.
Together we can prevent abuse and protect your rights.